Alerting on Incidents
After Investigating and Triaging Critical Incidents, setting up proper alerting ensures your team is notified immediately when critical incidents or anomalies are detected in your data. In Validio,
- Notification channels send messages to communication tools like Slack or Microsoft Teams.
- Notification rules define the conditions that trigger alerts to these channels.
If you are already using Slack for team collaboration, routing Validio alerts to a Slack channel provides seamless integration with your existing workflow. In this tutorial, you will set up alerting for critical incidents to a Slack channel.
Prerequisites
Before adding a notification channel in Validio, create and configure a bot app in Slack to communicate with Validio. This bot app needs to be added to the Slack channel that receives the notification messages from Validio. Refer to Setting up a Slack App for Validio.
Add a Notification Channel for Slack
Follow these steps to create a Validio channel to send notifications to a specific Slack channel:
- Navigate to Notifications > Channels and click + New Channel.
- From the Channel type list, select Slack.
- Select the Namespace where the channel will be created.
- Enter the Name, Channel ID, Bot Token, App Token, and Application Link URL to configure the channel.
- (Required) Enable Interactive Messages to manage or triage the incident from the notification message sent to Slack.
- (Optional) Click Test channel to verify your configuration.
- Click Create.
Once your notification channel is configured, set up rules that define when and how alerts are sent.
Add Notification Rules for your Channel
Follow these steps to create a rule that routes critical incidents to your Slack channel.
- Navigate to Notifications > Rules and click + New Rule.
- Under Channel,
- Select the Channel type: Slack
- Select the Namespace.
- Specify the Validio notification Channel you will route alerts to.
- Under Config, enter a Name, such a "Critical Incidents".
- Define Conditions:
- Add the first condition:
- Condition type: Create Type condition
- Issue type: Validator Incident
- Click Add
- Add the second condition:
- Condition type: Create Severity condition
- Incident severity: High
- Click Add
- Add the first condition:
- Click Continue to save this rule.
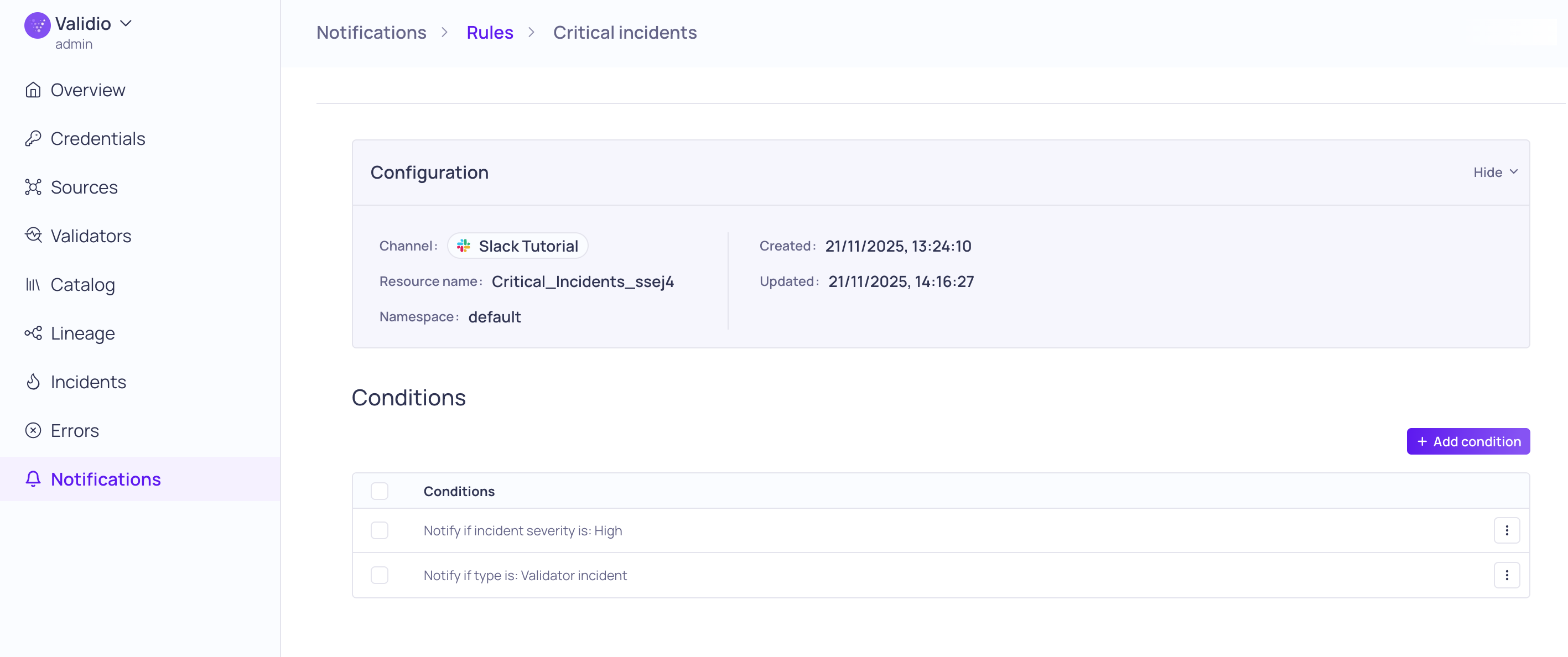
Configuration and conditions for "Critical Incidents"
Reviewing and Interacting with the Notification
When a critical incident triggers your notification rule, your team will receive a comprehensive alert message in the designated slack channel. Understanding what information is included in these notifications helps ensure your team can respond quickly and effectively.
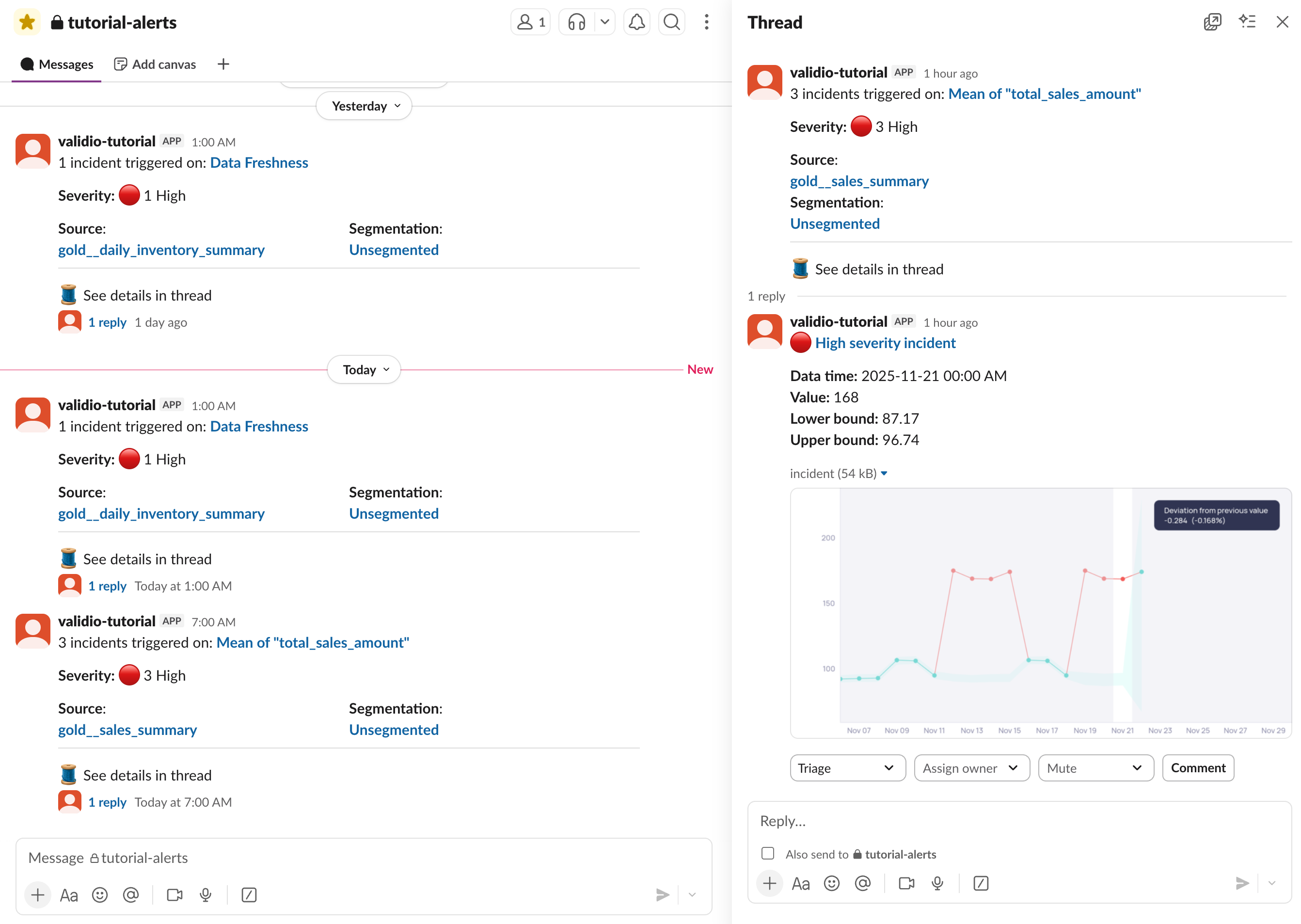
Reviewing details for a "Critical Incidents" notification
Each notification message provides essential details to help your team assess and respond to incidents.
- Review the Incident summary, which includes:
- Title: Indicates the number of incidents and which validation check failed, 3 incidents triggered on Mean of "total_sales_amount"
- Severity Level: Visual indicator showing the urgency (High, Medium, Low)
- Source and Segmentation: Which system or dataset is affected
- Timestamp: When the incident was detected
- Metric graph: Shows the current incident group as well as past, if there are any
- Impact assessment: A tooltip in the metric graph provides a brief description of what data quality issue was detected.
- Since you enabled Interactive Messages during channel setup, team members can take immediate action directly from the Slack notification:
- View Details: Opens the full incident report in Validio
- Acknowledge: Update the status from Triage to Investigating to mark that someone is taking this action
- Assign owner: Designate a team member to handle the incident
- Add Notes: Add comments and include initial observations or next steps. These comments will sync to the Activity log for the incident group within Validio.
- Follow up with your investigation within Validio. See Triaging Critical Alerts.
Validio's alerting is designed to keep you informed without causing alert fatigue. For more information, see About Notifications.
Next Steps
This Getting Started Tutorial helped you to quickly set up Validio to automatically monitor and alert on your data, enabling root cause analysis to highlight the impact of incidents so you can solve data quality issues faster.
Learn about more Validio features in the product documentation.
Updated 3 months ago