Managing Users and Identity Providers
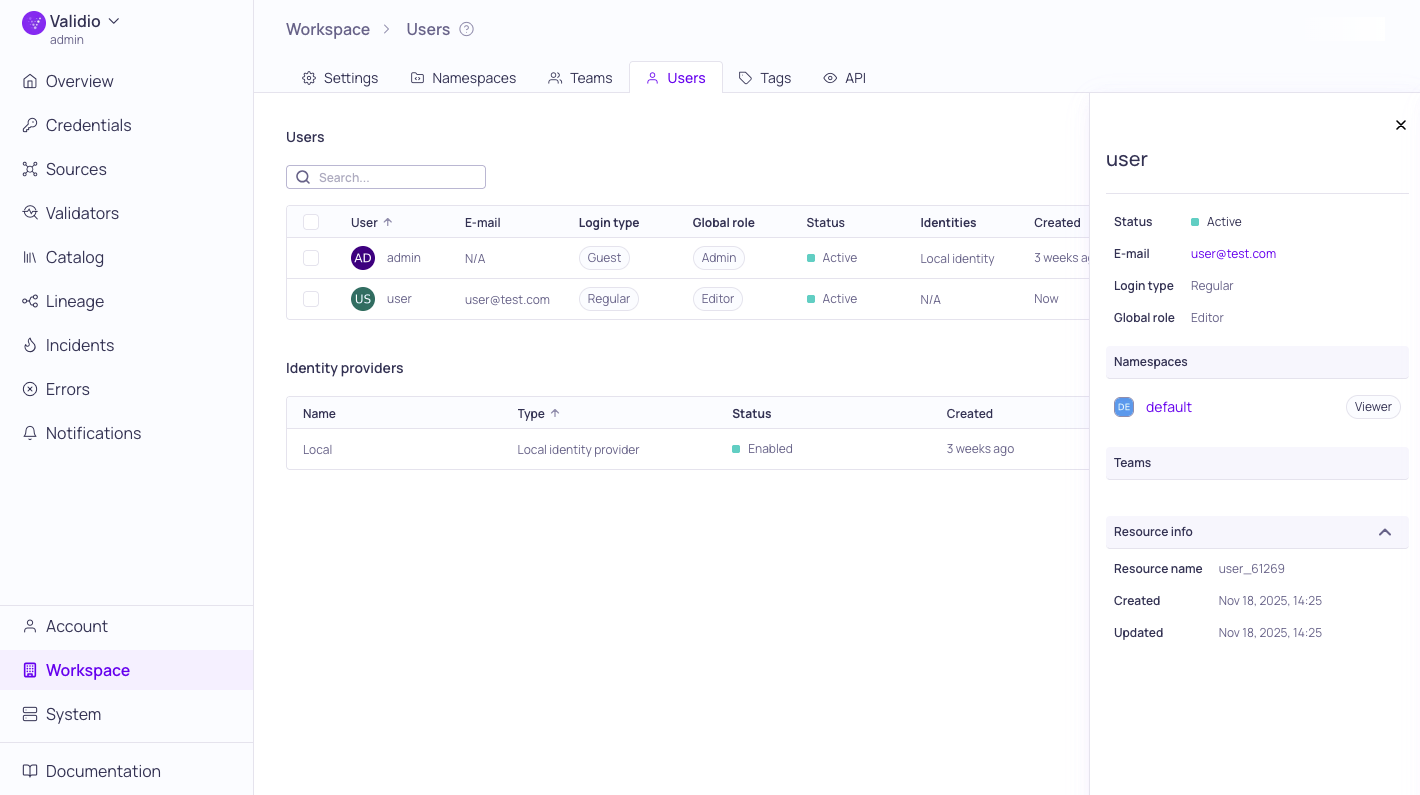
Workspace > Users with details panel
In the Workspace > Users settings, you can create and manage user accounts and configure identity providers for authentication in Validio.
Configure authentication using:
- Local identity provider - If you already have a Local identity provider configured, you won't see this option. You can only create one Local identity provider on a Validio installation.
- SAML identity provider - To allow users to authenticate using Okta, Google, Entra ID, and other SAML 2.0 providers.
Only Admins can update user accounts.
Add a New User
The Users section lists users created in your Validio system. For each user, it displays information on access privileges, status, associated identities, and creation date.
To create a new user,
- In Workspaces > Users, click + Add user.
- Under Configure details, fill in the configuration parameters. See User Configuration Parameters.
- (Optional) Check Create username and password to manually assign credentials.
- Click Create user.
User Configuration Parameters
| Field | Description |
|---|---|
| Display name | User identifier in Validio |
| Full name | User's first and last name |
| User's email address (validated to ensure it matches the standard format) | |
| User status | Active, Pending (has not logged in), or Inactive (cannot log in) |
| Login type | Guest or Regular. See Login Types |
| Global role | Viewer, Editor, Admin, or a Custom role. See Global Roles |
| Create username and password for this user | (Optional) Manual credential assignment |
Login Types
Login types provide users the following capabilities:
| Role | Viewing capabilities | Modifying capabilities |
|---|---|---|
| Guest | All, except Identity providers and API Keys | None |
| Regular | Based on assigned Role | Based on assigned Role |
Users can log in as Guest using their username and password, even if the Local identity provider is disabled. The Guest login type can be used to provide access to external support users who are not part of your SSO provider.
Global Roles
A user's global role provides the following viewing and modifying capabilities:
| Global Role | Viewing capabilities | Modifying capabilities |
|---|---|---|
| Admin | All | All |
| Editor | API keys, Identity providers, Namespaces, Roles, Settings, Tags, Teams, Users | Catalog assets, Searches, Lineage, Tags |
| Viewer | All | None |
| Custom | User-defined | User-defined |
The users capabilities can be overridden by Team and Namespace assignments. For more information, see Managing Roles.
You can also set a default user role automatically assign to all new users added to your workspace. For more information, see Configuring Global Settings.
Update and Delete Users
Click the ⋮ menu to:
- Update to modify the user details, status, or role.
- Delete to remove the user.
Add a New Identity Provider
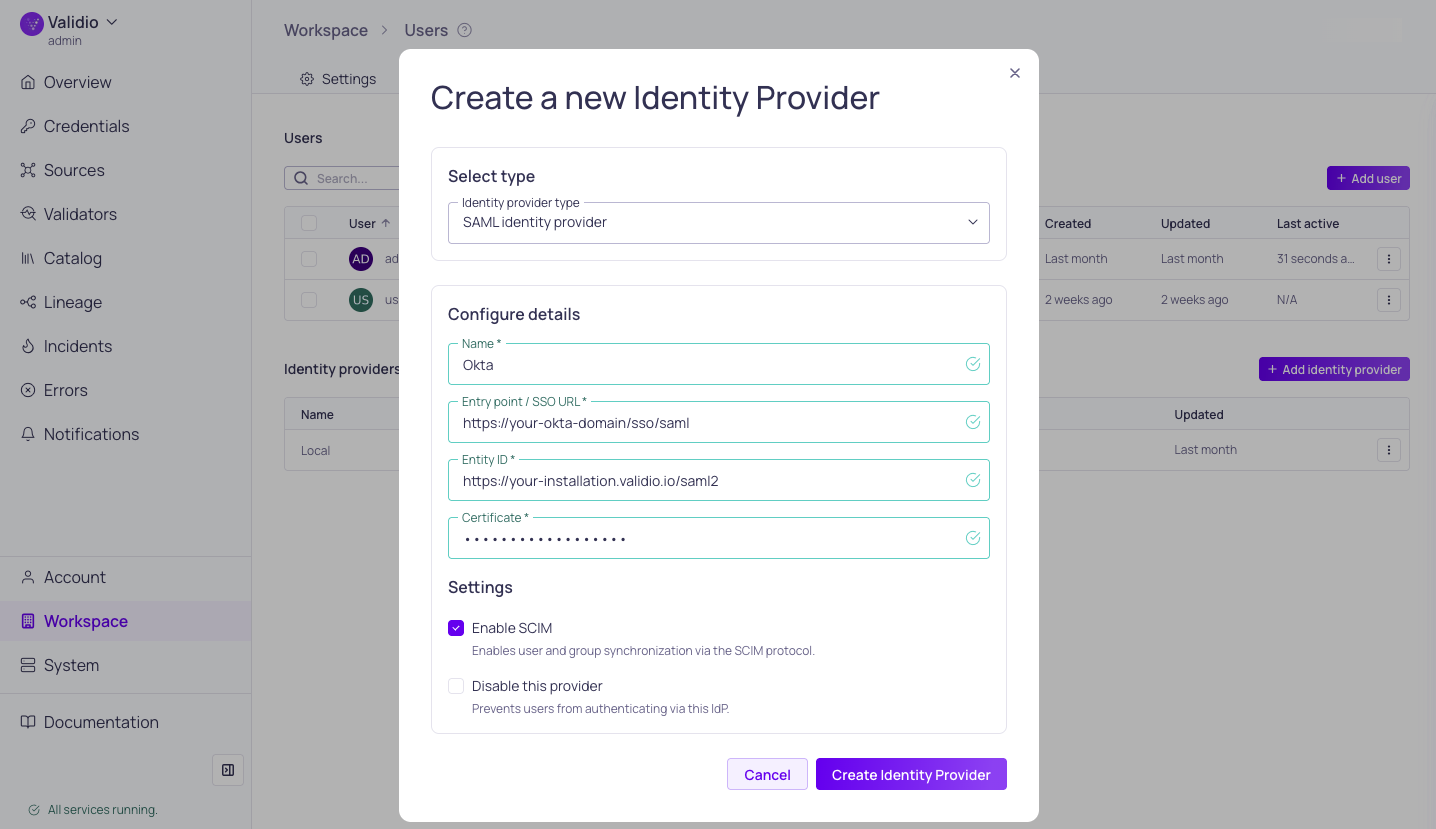
Configuring identity provider with SCIM
The Identity provider section lists identity providers configured on your Validio system. For each identity provider, it displays status, type, and dates for creation and last updated.
To configure a new identity provider,
- In Workspaces > Users > Identity Providers, click + Add identity provider.
- Under Select type, select either Local identity provider or SAML identity provider (SAML 2.0).
- Under Configure details,
- Fill in the required parameters. See Identity Provider Configuration Parameters.
- (Optional) When configuring a SAML identity provider, check Enable SCIM to enable user and group synchronization via the SCIM protocol.
- Copy or save the generated SCIM API Key to configure user provisioning in your identity provider. See SCIM Synchronization.
- (Optional) Check Disable this provider to prevent users from authenticating with this identity provider. You can enable it later by updating the identity provider.
- Click Create Identity Provider.
Identity Provider Configuration Parameters
The following fields are required when adding or updating an identity provider.
| Parameter | Description |
|---|---|
| Name | Unique display name in Validio |
| Entry point / SSO URL | SSO URL or Location URL for the configured identity provider |
| Entity ID | https://YOUR-INSTALLATION.validio.io/saml2 |
| Certificate | Identity provider certificate (plain text) |
SCIM Synchronization
SCIM, or System for Cross-Domain Identity Management, enables large organizations to automatically provision and de-provision users and groups using external identity providers like Okta or Entra ID, eliminating the need to duplicate work in Validio.
- Syncing Users and Groups: Users and groups assigned in the identity provider are imported into Validio. For example, pushing the "validio admins" group from Okta will create a corresponding team in Validio, and users in that Okta group will be added to the Validio team.
- De-provisioning: When a user is removed from the identity provider (like Okta), they are automatically set to inactive in Validio (not deleted). Inactive users cannot log in.
Validio teams have a global role, allowing for easier management of global permissions for groups synced from the identity provider. See Managing Teams.
Configuring SCIM
Prerequisite: In your Validio Workspace Settings, set an Application URL. If the Application URL is not set, you cannot enable SCIM.
In the external identity provider, configure the following:
- SCIM API key: Enabling SCIM in the Validio SAML identity provider configuration generates a unique SCIM API key that you will configure in the external identity provider as the Bearer authentication token.
- Base URL: The connector URL used to communicate with your Validio installation. This base URL is formatted:
https://YOUR-INSTALLATION.validio.io/scim/v2The name of this setting may be different depending on the identity provider. For example, "SCIM connector base url" in Okta and "Tenant URL" in Entra ID.
- Provisioning Actions: Select the provisioning actions you want to enable for your SCIM configuration.
Supported SCIM Actions
Validio supports the following types of SCIM provisioning actions configured on the identity provider:
- Push new users - When you create a new user in your identity provider, sends a SCIM request to add the new user to Validio.
- Push profile updates - When you change user attributes in your identity provider, sends a SCIM request to update corresponding users in Validio.
- Push groups - When you assign groups in your identity provider, sends a SCIM request to create Teams with corresponding memberships in Validio.
Update and Delete Identity Providers
Click the ⋮ menu to:
- Update to modify Name, enable/disable the provider.
- Delete to remove the identity provider.
Updated about 2 months ago