Customer Virtual Private Cloud
When data cannot leave your environment.
A Customer Virtual Private Cloud (VPC) deployment installs Validio in your own Kubernetes cluster, ensuring that your data never leaves your environment.
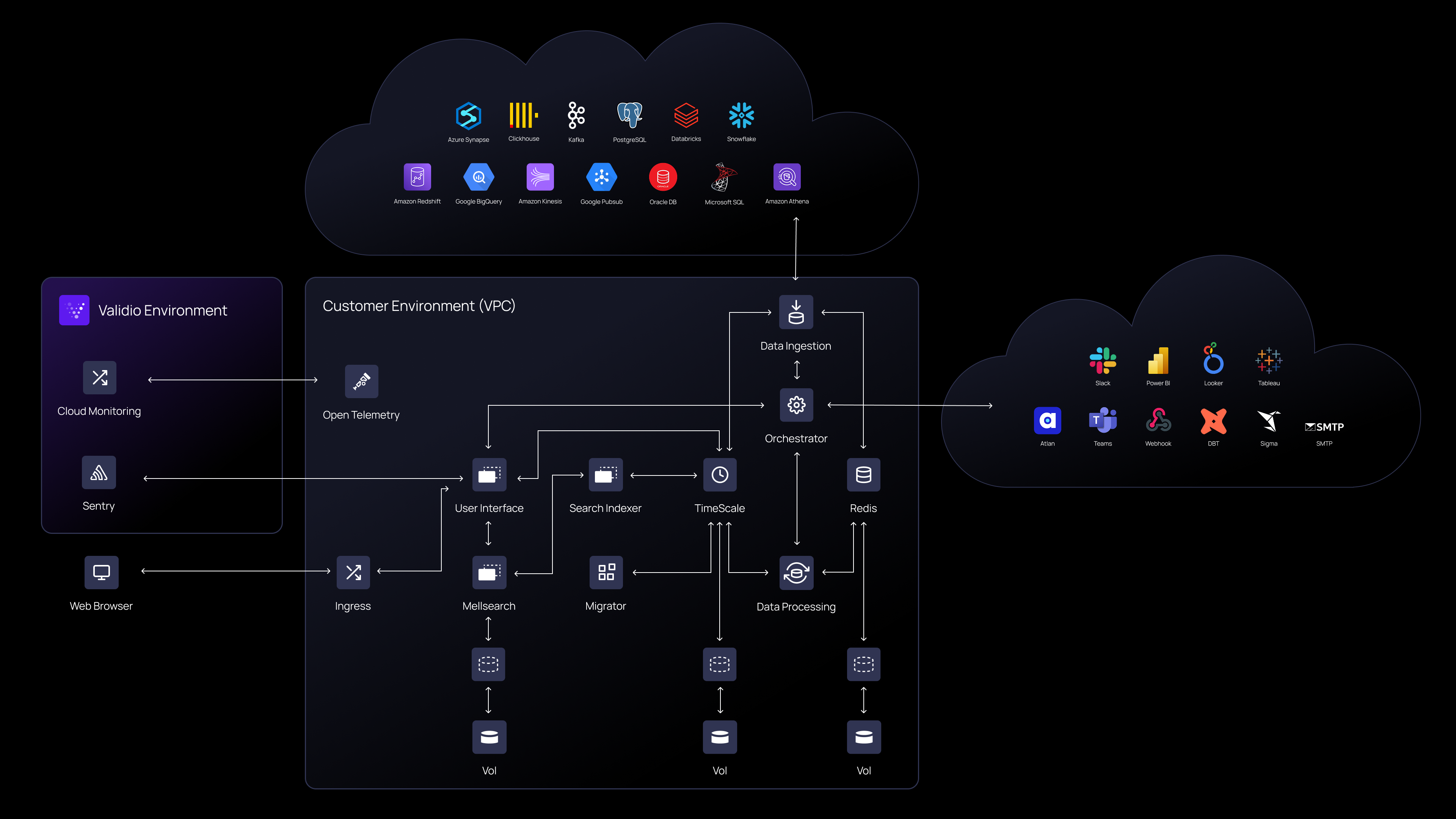
With this approach you will install Validio in your own Kubernetes cluster and your data will never leave your environment.
In a Customer Virtual Private Cloud (VPC) deployment, Validio grants the customer access to the Validio Helm chart and container images. The customer can then download and install the Validio Helm chart on Google (GCP), AWS (EKS) or Azure (AKS) clusters.
While Validio offers support under agreed upon service levels, the customer needs adequate in-house DevOps resources. Since Validio has no access to the infrastructure, these DevOps resources must manage the infrastructure and maintenance of the Kubernetes cluster. This includes collecting and acting on metrics from the infrastructure. The Customer is also responsible for maintaining and updating their Validio platform.
Refer to the following guides for installing and configuring your VPC deployment:
Managed SolutionThe Validio Managed Solution is a popular deployment alternative since it allows customers to focus their engineering resources on business value driving activities.
Updated 8 days ago